Modular Math and the Shift Cipher
Shift Ciphers work by using the modulo operator to encrypt and decrypt messages. The Shift Cipher has a key K, which is an integer from 0 to 25. We will only share this key with people that we want to see our message.
How to Encrypt:
For every letter in the message M :
1. Convert the letter into the number that matches its order in the alphabet starting from 0, and call this number X.
( A=0, B=1, C=2, ...,Y=24, Z=25)
( A=0, B=1, C=2, ...,Y=24, Z=25)
2. Calculate: Y = (X + K) mod 26
3. Convert the number Y into a letter that matches its order in the alphabet starting from 0.
(A=0, B=1, C=2, ...,Y=24, Z=25)
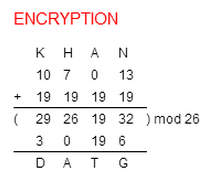
For Example: We agree with our friend to use the Shift Cipher with key K=19for our message.
We encrypt the message "KHAN", as follows:
We encrypt the message "KHAN", as follows:
So, after applying the Shift Cipher with key K=19 our message text "KHAN" gave us cipher text "DATG".
We give the message "DATG" to our friend.
How to decrypt:
For every letter in the cipher text C :
1. Convert the letter into the number that matches its order in the alphabet starting from 0, and call this number Y.
(A=0, B=1, C=2, ..., Y=24, Z=25)
(A=0, B=1, C=2, ..., Y=24, Z=25)
2. Calculate: X= (Y - K) mod 26
3. Convert the number X into a letter that matches its order in the alphabet starting from 0.
(A=0, B=1, C=2, ..., Y=24, Z=25)
(A=0, B=1, C=2, ..., Y=24, Z=25)
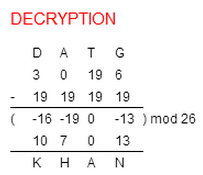
Our friend now decodes the message using our agreed upon key K=19. As follows:
So, after decrypting the Shift Cipher with key K=19 our friend deciphers the cipher text "DATG" into the message text "KHAN".
Why is the Shift Cipher insecure?
A cipher should prevent an attacker, who has a copy of the cipher text but does not know the key, from discovering the contents of the message. Since we only have 26 choices for the key, someone can easily try all of the 26 keys, one by one, until they recover the message. This type of attack is called a brute force attack.
HILL CIPHER
step1: Treat every letter in plain text as a number so that A=0,B=1,...Z=25.
step2:Now our plain text matrix is multiplied by a matrix of randomly chosen keys.The key matrix consists of nxn,where n is the number of rows in our plain-text matrix.
step3: Now multiply two matrices.
step4: Now compute a mod 26 value of resultant matrix.
step 5:Translate the numbers to alphabets. For eg 5=F,8=I etc.
step1: Treat every letter in plain text as a number so that A=0,B=1,...Z=25.
step2:Now our plain text matrix is multiplied by a matrix of randomly chosen keys.The key matrix consists of nxn,where n is the number of rows in our plain-text matrix.
step3: Now multiply two matrices.
step4: Now compute a mod 26 value of resultant matrix.
step 5:Translate the numbers to alphabets. For eg 5=F,8=I etc.